How do I use the real-time protection shields in Malware Protector?
Malware Protector offers Real-Time (always on) Protection Shields for round the clock protection of your PC.
The Real-Time Protection Shields if enabled (only in the Registered Version) serve the purpose of restricting the malware attacks in real time. Malware programs trying to enter the system are identified and stopped as and when detected by the program. Alerts are triggered as soon as the tool encounters malware trying to install or execute on the system. It is up to the user to allow the program to run on the system or block/discard it completely.
There are 2 shields that protect the system from malware threats round the clock:
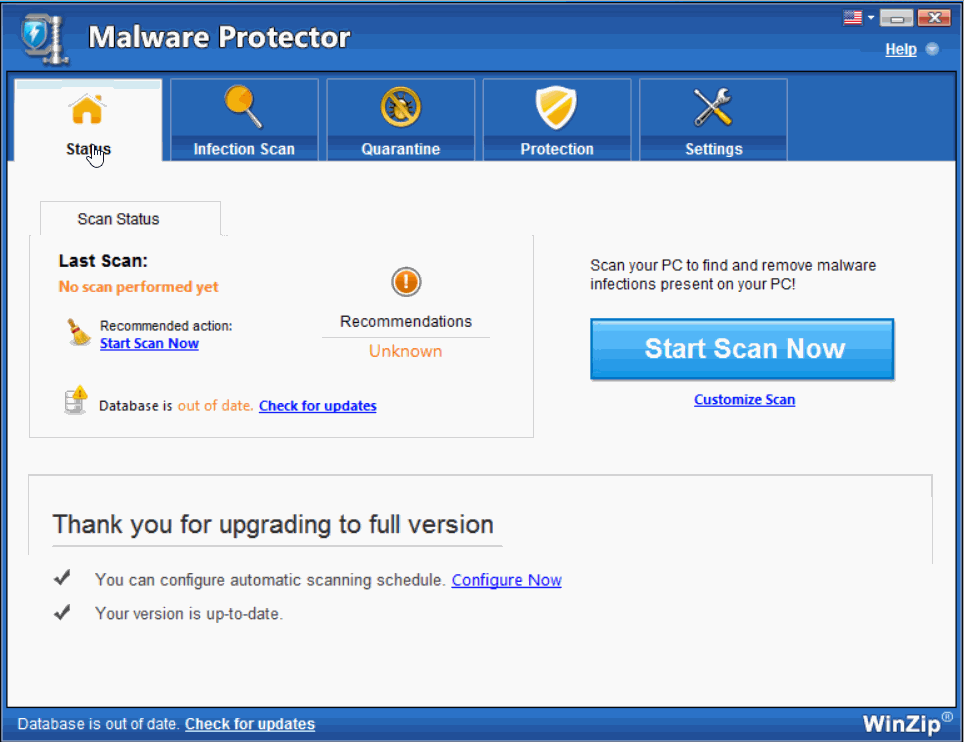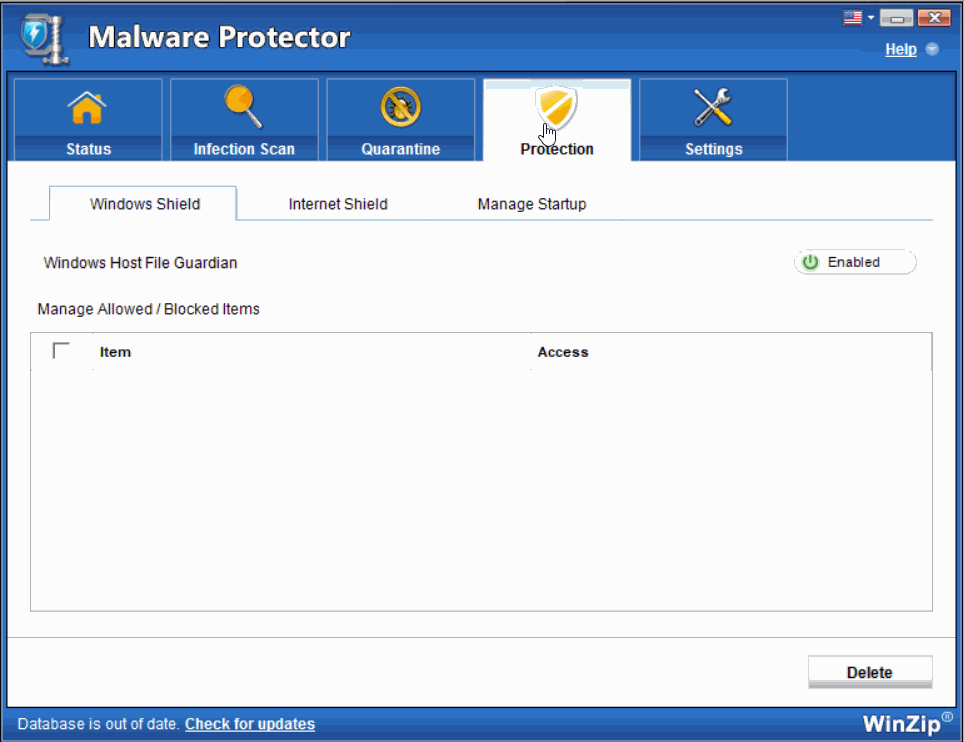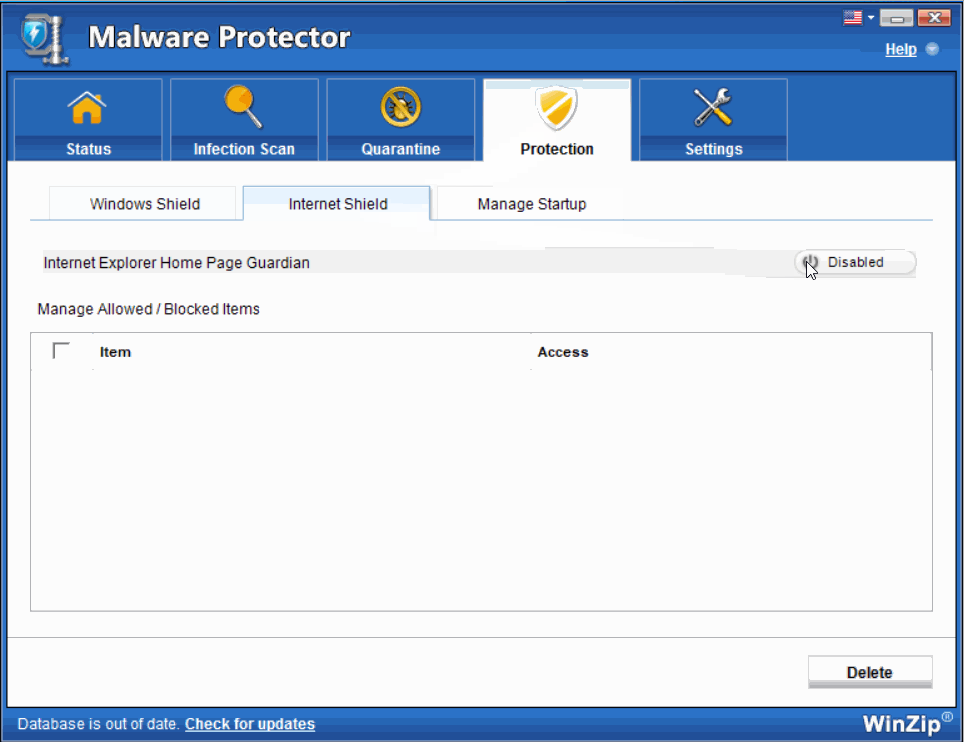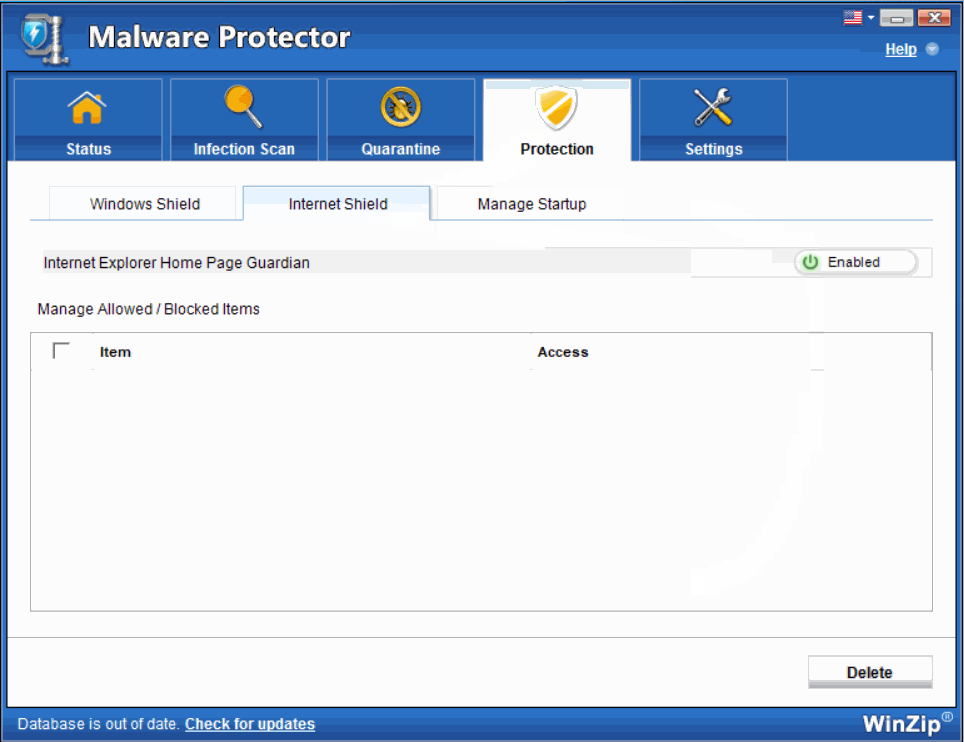
- Windows Shield- Windows Host File Monitor
Host File in Windows is a file used to maintain the host names mapped against their IP addresses. Host Files are referred to find out the associated IP addresses for any host names. In case the desired IP addresses are not found, the operating system asks the Domain Name System (DNS server) for the information. These files can be used to block sites locally instead of blocking the servers. Some malware are created to make changes to these Windows Host Files. This particular shield alerts the user when such malicious activities are attempted in the Windows Host Files.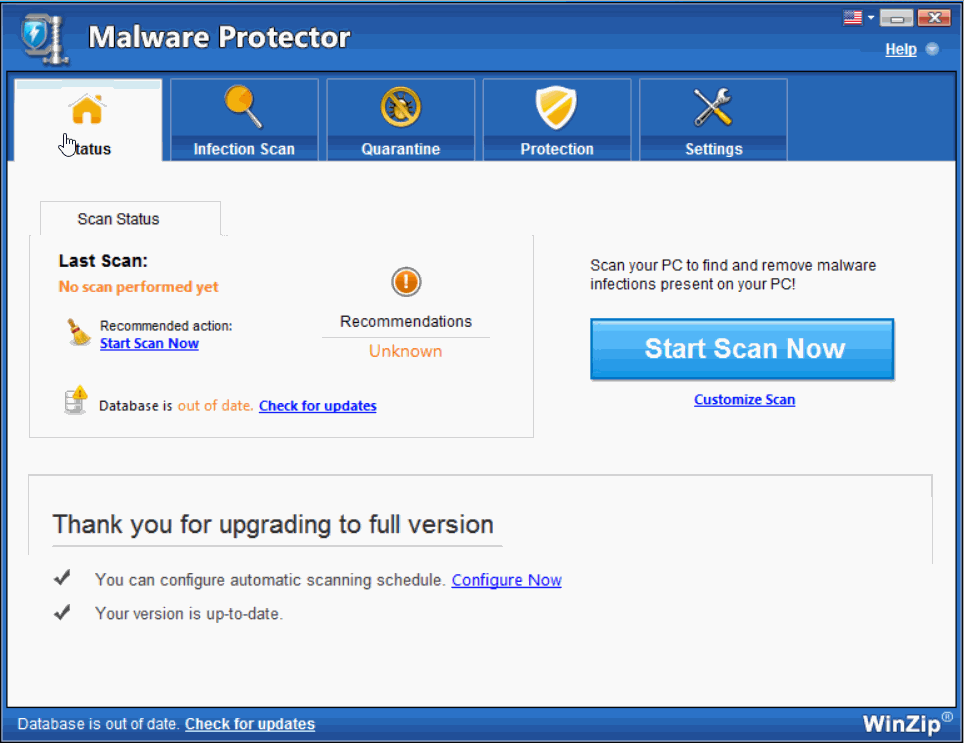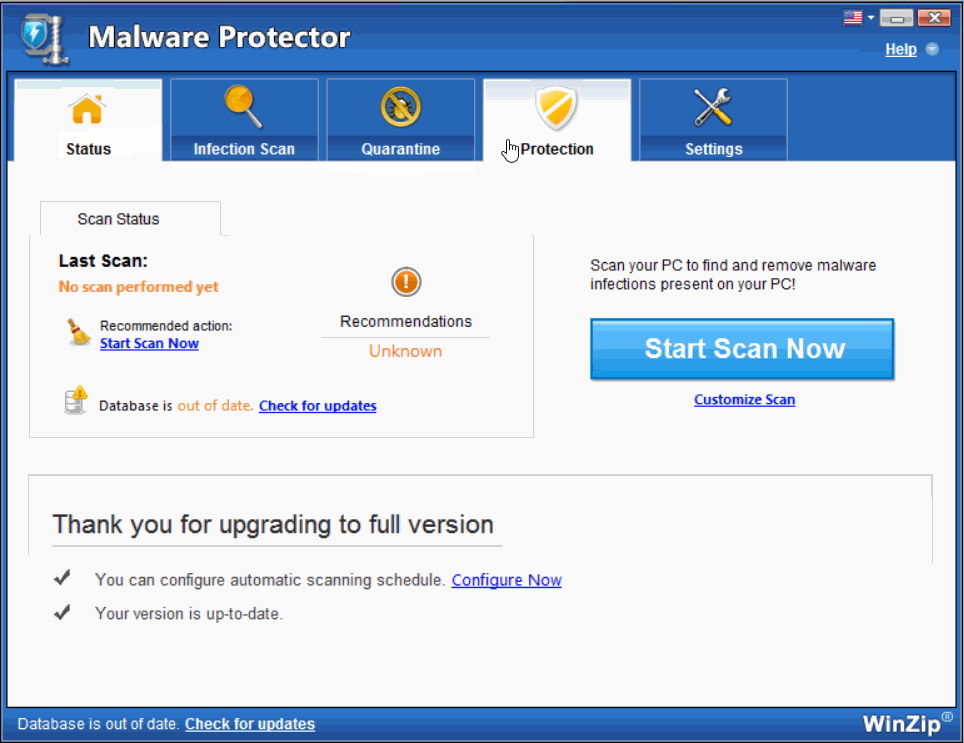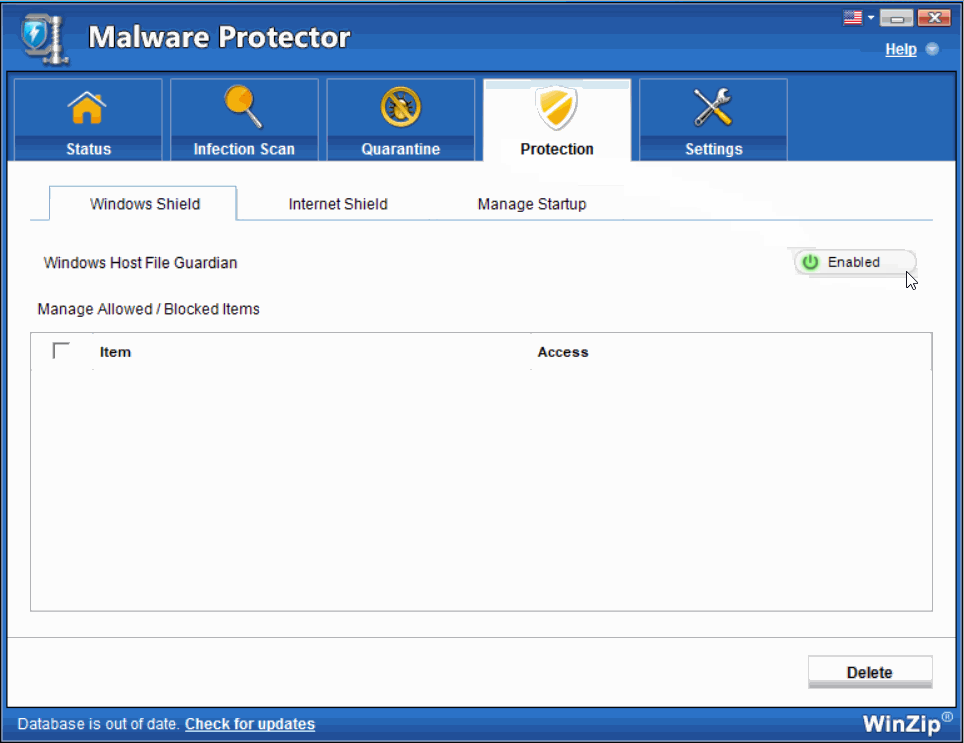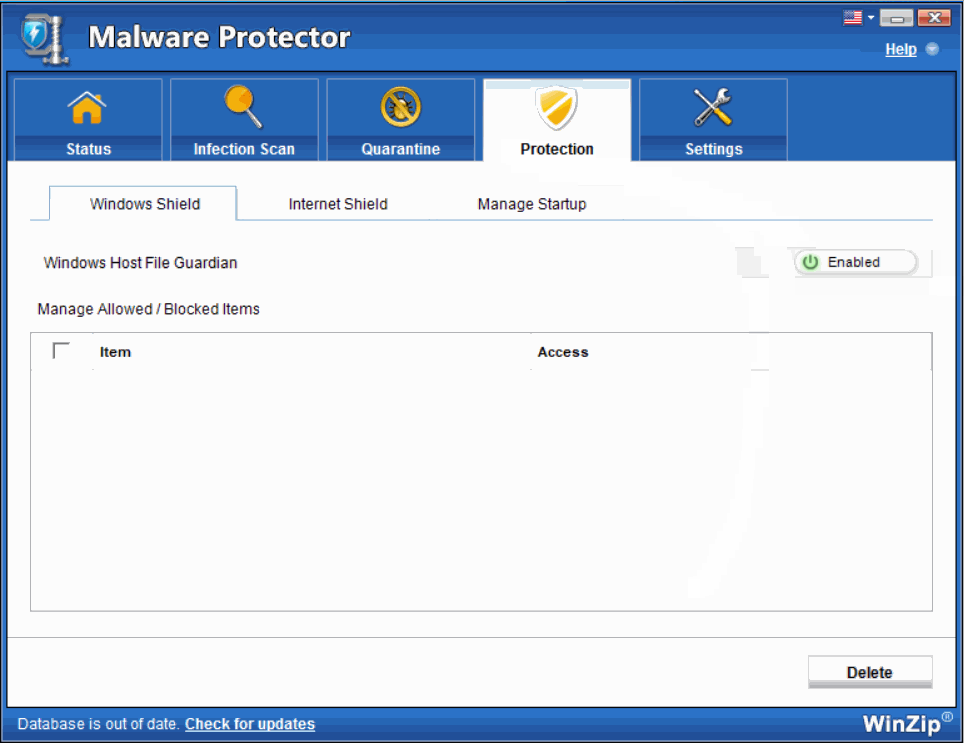
Select Enabled to enable the real time Protection Windows Shield for round-the-clock protection.
When there is an intrusion attempt by any unknown or malicious program, the shields alert the user of this attempt through a pop-up message. It is then the user’s decision to allow the unknown program to run on the system.
• Allow – Select the ‘Don’t ask me again’ option and then click on ‘Allow’ button if you trust the application/program and wish to execute the program on the system. All the sessions when you allowed the applications to run on the system will be listed under the “Windows Shield” tab.
• Block – Select the ‘Don’t ask me again’ option and then click on ‘Block’ button if you do not find the application authentic and do not wish it to run on the system. All the sessions when you blocked the application to execute on the system will be listed under the “Windows Shield” tab.
- Internet Shield- Internet Explorer Home Page Guardian This particular shield prevents unauthorized alterations in the IE toolbars and its functionalities by any malicious malware.The Internet is the biggest medium through which malware programs install themselves on the system. Internet Shields prove to be very useful in detecting malware in real time before they can cause any harm to the system.
Select Enabled to enable the real time Protection Internet Shield for round-the-clock protection.
When there is an intrusion attempt by any unknown/malicious program, the shields report the user of the same through a pop-up message. It is solely up to the user to allow the unknown program to run on the system or not.
• Allow – Select the ‘Don’t ask me again’ option and then click on ‘Allow’ button if you trust the application/program and wish to execute the program on the system. All the sessions when you allowed the applications to run on the system will be listed under the “Internet Shield” tab.• Block – Select the ‘Don’t ask me again’ option and then click on ‘Block’ button if you do not find the application authentic and do not wish it to run on the system. All the sessions when you blocked the application to execute on the system will be listed under the “Internet Shield” tab.
- Manage Allowed/blocked items
Programs/applications, you allow or block will be listed here under their respective tabs. To remove unneeded events from the list, click on the “Delete” button.
